The passive survey uses a surveying system to hearken to the WiFi environment. Typically, the software used for these surveys is configured to scan specific channels and WiFi networks so as to measure the sign power and noise levels https://ru.wikipedia.org/wiki/EPAM_Systems. Using the data gathered in the course of the predictive survey, a web site survey is carried out to gather additional details about the campus and determine if the design can meet necessities.
However, the safety which of the next enterprise wi-fi deployment fashions of these technologies isn’t properly established and a few mechanisms have been breached. In addition, these mechanisms are costly and not scalable, as they require hardware deployment on the client aspect. Commercial Virtual Private Network (VPN) services have flip into a popular and handy expertise for purchasers looking for privateness and anonymity. However, as of but, the claims made by these suppliers haven’t acquired a sufficiently detailed scrutiny.
– Understanding Enterprise Network Security Architecture
The proposed scheme retains checking the obtainable bandwidth of the entire potential wi-fi routers in a time interval and choose essentially essentially the most obtainable one. If a brand new shopper appears, basically essentially the most obtainable router is visible to him or her whereas the others are https://www.luxoft.com/ not seen. Here at SecurEdge Networks, we provide a service to supply community solutions to businesses that packages all of the above industrial\enterprise capabilities right into a subscription model. Enterprise wi-fi networks should carry out to a level a lot larger than consumer environments.
Regardless of the deployment mannequin chosen, Wireless Sync offers a single, constant user interface, minimizing the help burden and maximizing user productiveness. This is a instructional model which of the following enterprise wireless deployment models to supply insight into what’s going on with all elements of wi-fi connectivity and mobility across healthcare and the enterprise space.
Additional website surveys are really helpful if any a part of an current community has being upgraded, if there have been structural adjustments to a facility, or if voice and roaming options weren’t optimized in the https://globalcloudteam.com/interesting-facts-about-cloud-deployment-models-and-their-features/ earlier deployment. The administration interface of a cloud WiFi system is entry via a browser and sometimes has fewer configuration choices compared to an on-premises controller / administration system.
- Using Prime Infrastructure to Manage Wireless Networks (PIMWN) is an up to date mannequin of the (NMENPI and WMNGI ).
- As clients start to shift between Ethernet and Wi-Fi throughout the workday, it is smart to use VLANs to both wired and wi-fi community access.
- This course teaches you recommendations on tips on how to design, set up, configure, monitor, and conduct major troubleshooting duties on a Cisco WLAN group of any dimension.
- The Understanding Cisco Wireless Foundations (WLFNDU) course provides you the knowledge and abilities you should place, plan, implement, function, and handle a Cisco WLAN network.
- WatchGuard APs can routinely uncover and connect with W-Fi Cloud as quickly as they’re powered up and obtain Internet entry.
- This examination exams your data of wireless community design, including site surveys, wired and wi-fi infrastructure, mobility, and WLAN high availability.
The goal of this content is to offer know-how info, awareness, and path to assist remodel the enterprise in 2020 via all features of wireless connectivity, mobility, and cybersecurity. This examination which of the following enterprise wireless deployment models exams your data of wi-fi neighborhood implementation, along with FlexConnect, QoS, multicast, advanced location providers, safety for consumer connectivity, monitoring, and gadget hardening.
Wlc Discovery
However, relying on the form of the power, this design doesn’t all the time work. There may also which of the following enterprise wireless deployment models be mounting limitations that have an effect on the placement and design of the APs.
Wlcs
This paper thus investigates the claims of privateness and anonymity in industrial VPN providers. We analyse 14 of essentially the most nicely-appreciated ones, inspecting their internals and their infrastructures. The VPN suppliers route the client’s traffic over an encrypted tunnel to a VPN gateway within the cloud. The Short Message Service (SMS) deployment structure https://globalcloudteam.com/ dictates that messages be routed through a Short Message Service Center (SMSC) from the equipment server to the wi-fi system (as depicted in Figure 10-6). Internet Protocol (Web) communication is at current used proper now within the wired world with standardized safety by way of SSL encryption.
PCs connect to the application server immediately with degree-to-point privateness utilizing HTTPS, which is HTTP working over an SSL-secured hyperlink (Figure 10-3). The different is that the useful resource utilization of the whole wi-fi routers turns into very low. In order to resolve the problems, we propose a load sharing scheme to maximise community bandwidth utilization primarily based totally on SSID(Service Set IDentifier) hiding.
– Using Network Analysis Tools
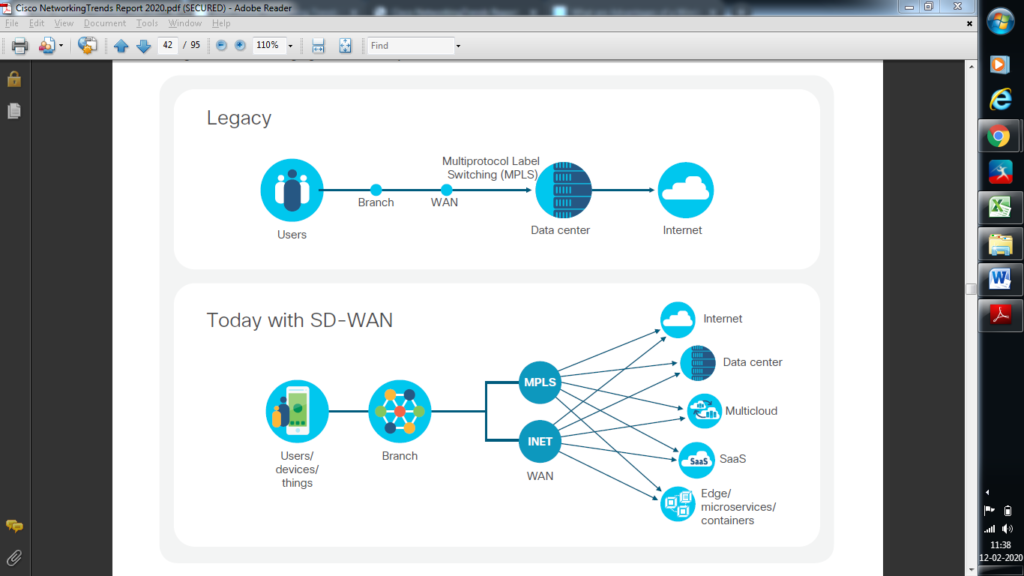
reveals a high stage diagram of a primary centralized WLAN architecture, where LWAPP APs connect with a WLC through LWAPP. This chapter discusses the important thing design and operational considerations associated with an enterprise Cisco Unified Wireless deployment. Moving an wireless gadget between access points within the same wi-fi community. “We have discovered Trapeze’s Virtual Service Sets to be a really useful tool in our network,” stated Chris Hessing, Head of Networking on the J. Finally, there are phone items and third-celebration mechanisms that declare to offer voice encryption expertise that protects communication between two ends of the telephone dialog.




